Zero2Automated - January 2023 Challenge
We've been seeing a flow of first stagers flying around on Twitter in the form of a OneNote document, so why don't we all have a look..
This RE shitpost wasn’t sponsored by the OALabs Patreon, however if you don’t have it already go and check their awesome content out.
What the hell is a pointer? When I first started learning C and C++, that was the first question that popped into my head. Just like every malware reverse engineer starting out, I was pretty much confused on what they were, particularly since I wrote stuff in Python or C# all the time. As a newbie, I also hated writing in it:

I eventually learned how to use pointers, but not without a price. One day I saw this message on Discord, and it dawned on me about how true the statement was. Then I begun to remember some memes my friends and I shared with each other a while ago…

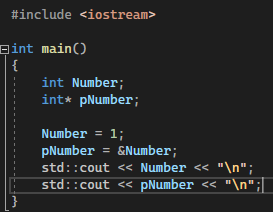
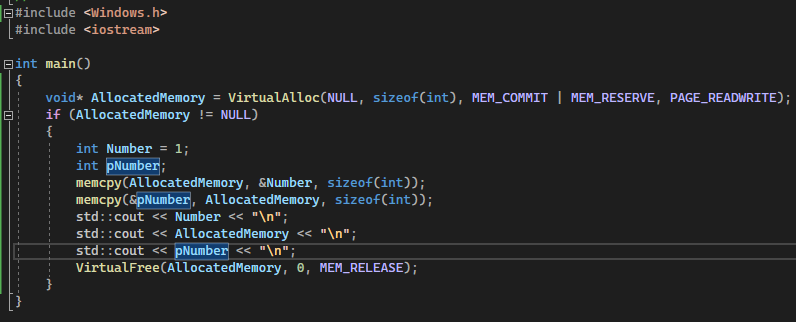
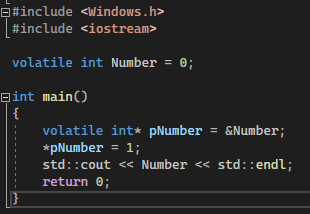
This one should be simple enough! Simply put, pointers point to variables containing value. Pointers themselves contain the memory address of the variable they point to, and can be dereferenced to retrieve the original value.

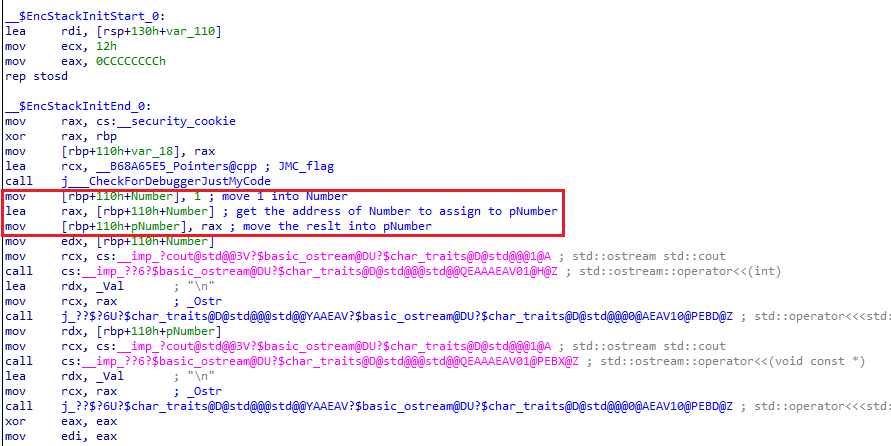
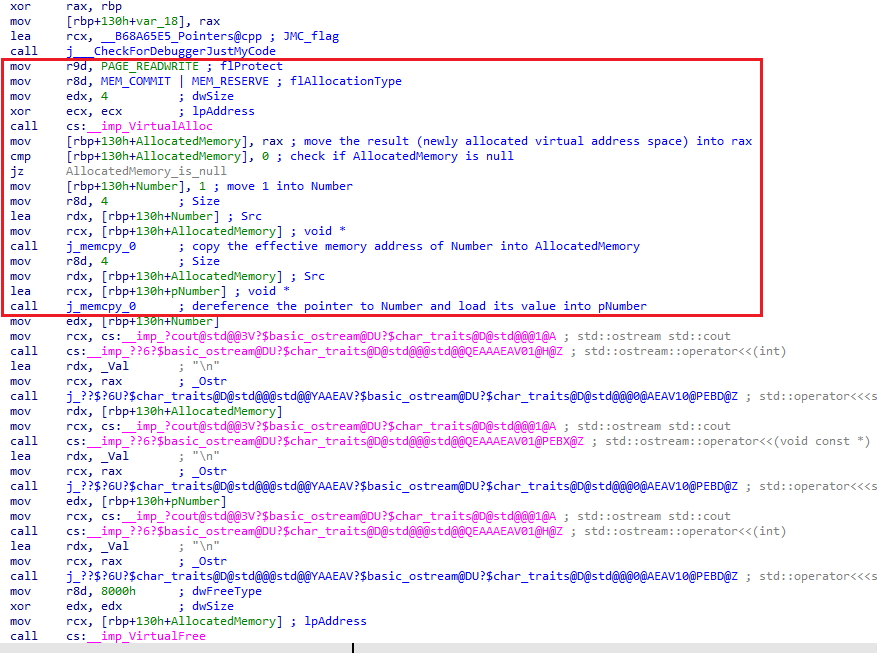
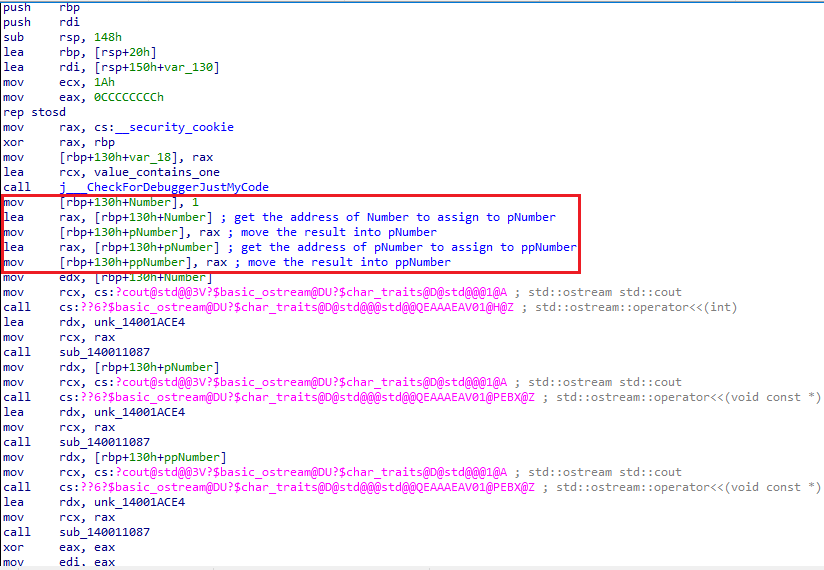
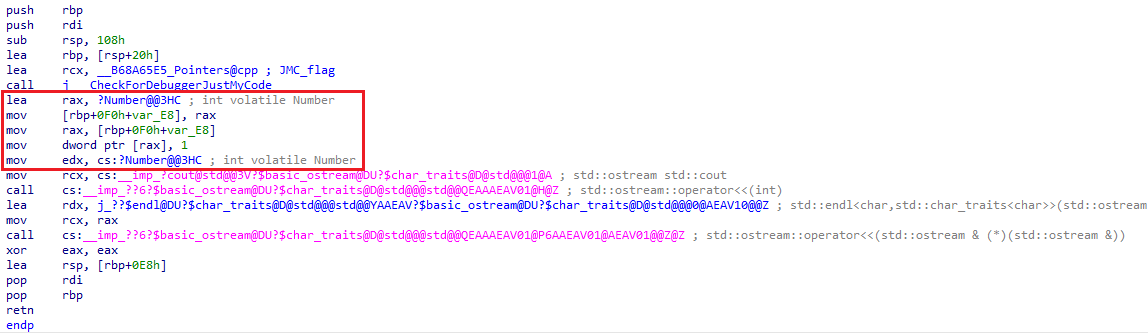
The int* type causes the compiler to define the pNumber variable as a pointer, which would later on contain the value of Number by calling it alongside the & dereferencing operator. Within the Assembly, you may also notice the lea instruction was used to apply the pointer:
 https://stackoverflow.com/questions/11626786/what-does-void-mean-and-how-to-use-it
https://stackoverflow.com/questions/11626786/what-does-void-mean-and-how-to-use-it
A void * type points to a memory location that can be converted/casted to any value type - be it a char, int, long, whatever you want the eventual variable type to be! PVOID and LPVOID are also happen to simply be Windows API typedef for the void* pointer. For examples when this pointer type is used, think of VirtualAlloc in malware when it is unpacking and allocates memory - the result returned would be a blank memory space with either read, write and/or execute permissions depending on the parameters that was passed to the function in the first place!
A similar approach can be taken for strings:
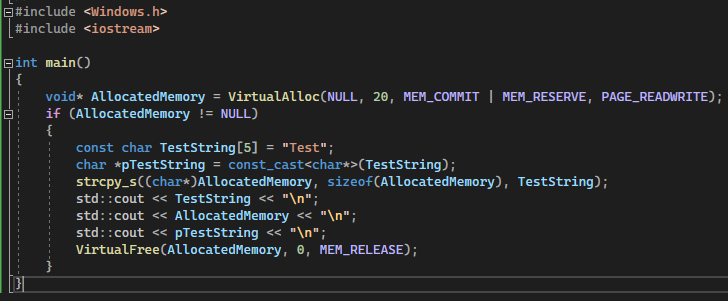
(Console output was practically the same as the last one)
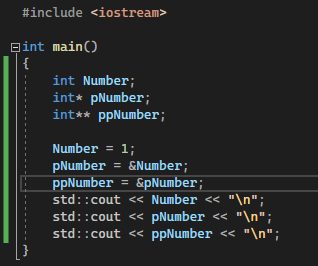
Within this example, we have two pointers - one that contains the memory address to the original integer value, and another that points to the other pointer (here we call it a pointer pointer). Reference

 “How did we even get here!?” - S1ren from Offensive Security
“How did we even get here!?” - S1ren from Offensive Security
https://stackoverflow.com/questions/9935190/why-is-a-point-to-volatile-pointer-like-volatile-int-p-useful
This pointer works very similarly to the one from the first section! There is only one difference. as quoted from the almighty MSDN:
The volatile keyword specifies that the value associated with the name that follows can be modified by actions other than those in the user application. Therefore, the volatile keyword is useful for declaring objects in shared memory that can be accessed by multiple processes or global data areas used for communication with interrupt service routines.
When a name is declared as volatile, the compiler reloads the value from memory each time it is accessed by the program. This dramatically reduces the possible optimizations. However, when the state of an object can change unexpectedly, it is the only way to ensure predictable program performance.
volatile pointers have their uses, but as of currently I’m not familiar with them. Technically speaking, the code below should be functionally the same as a regular pointer with minor differences, but in case you’re curious about (of course, why wouldn’t you be if you’ve kept reading up to this point?), here’s the before and after with the code when it gets uglified by IDA!

While this shit is funny as hell, I won’t be evaluating it!

The *(int *) part casts the variable number to a pointer to an integer type, then the * in front dereferences it (reference). I couldn’t reproduce this myself, but here’s some good docs to understand a bit more about casting, check out these articles:
https://learn.microsoft.com/en-us/dotnet/csharp/programming-guide/types/casting-and-type-conversions https://learn.microsoft.com/en-us/cpp/cpp/casting?view=msvc-170
That sums up the RE note for today! Before this gets out of hand, I will be seeing myself out:
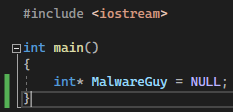
NULL (essentially 0x0) - used to terminate strings, programs and lives! You can see how that would be interpreted in Assembly:
Jokes aside, While this seemed like a programming post, I hope it would be helpful to those who are trying to make their way around reverse engineering so they don’t need to suffer like I once did! It was pretty fun to write up, and I applied some concepts I learned from Sergei’s OALabs Patreon and understood quite a bit more about pointers. For anyone who is already subscribed, make sure to leave some great feedback for him, as feedback helps content creator lives! Always spread goodness in someone’s days. In my opinion, I genuinely think he’s a cool guy and he explains overly technical concepts in a way that helps to people understand. Sergei if you’re still reading, I would like you to help me unpack VMP and Armadil-

Pointers offer powerful ways to manage memory (when used correctly). Instead of pushing a value to the stack or assigning it to a register, an argument can take in pointer variables and reference or make changes to the value rather than allocating additional more memory inside the program. This generally happens for several existing methods already, take VirtualAlloc and memcpy for example. Inside a debugger, if you want to keep track of the data inside a region of memory, simply follow the steps I did in this overly verbose post
Sometimes you may come across these especially if you attempt to decompile and read psuedocode, and it can be very confusing if you’re not familiar with C syntax. I myself would do a quick search to understand the behaviour and results of these types of code. Most of the time, you will be dealing with regular pointers, but make sure you keep this lifesaver right near you!

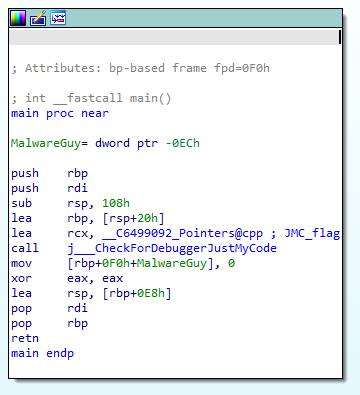
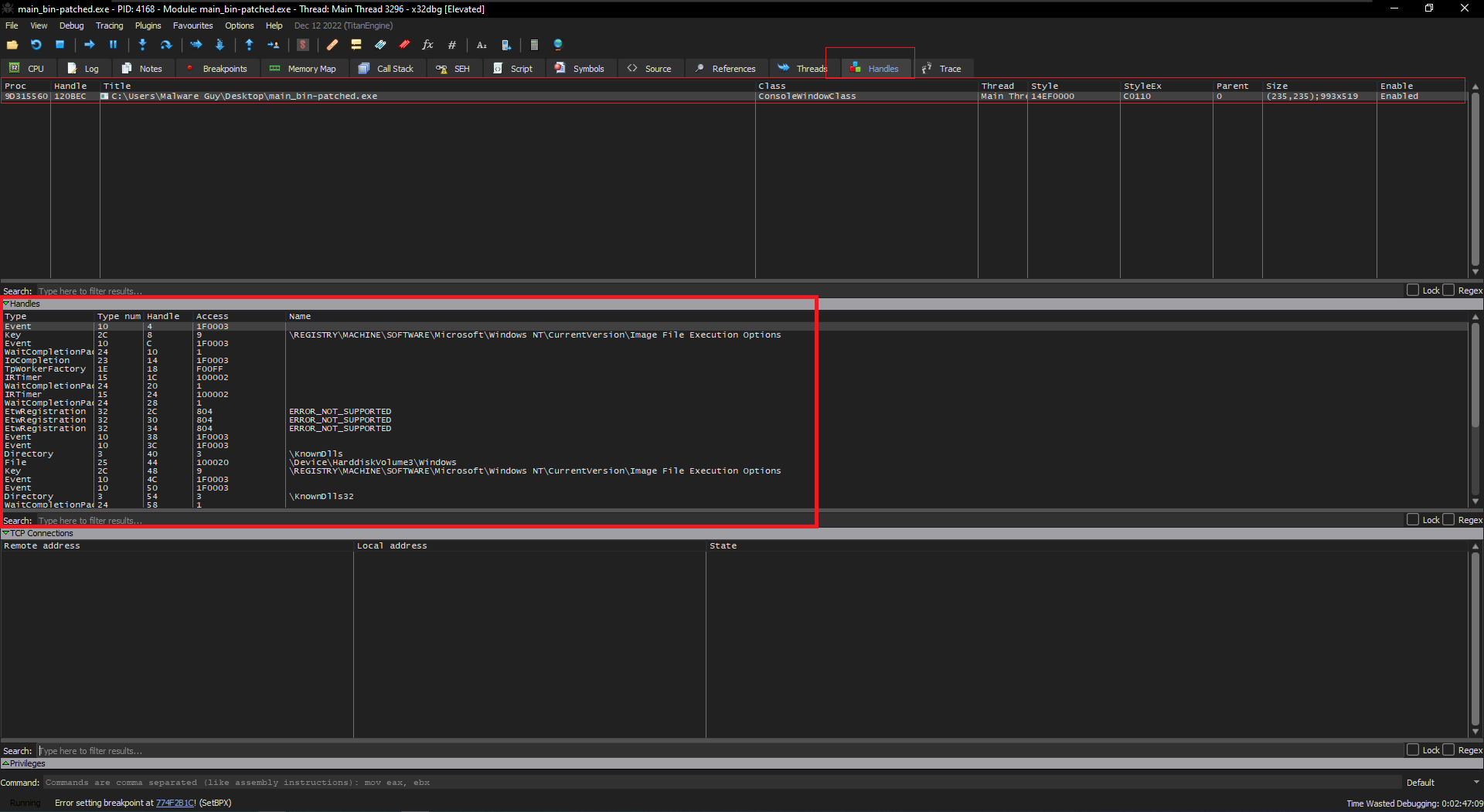
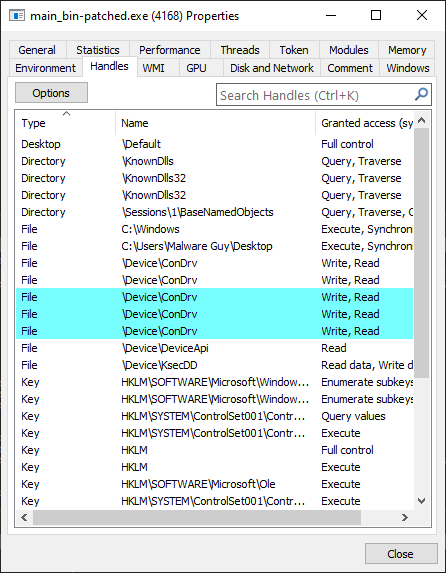
PS: A handle can be a pointer, but never exclusively. The same can’t be said for the other way round though, since a handle is meant to be built-in Windows functionality that provides access to an object (shamelessly nabbed from MSDN once again). You can check the handles that are open inside a process from x64dbg and Process Hacker/System Informer! Be sure to either search for them by their Name and/or Type, and Refresh if the window is empty inside the debugger:
Also for anyone who likes light mode Discord or obsessively codes in Java, I would like to have a word with you:

